A decent rundown of the issue. They didn’t mention Canadians also have a right to privacy protected by the Charter. I like the odds of C2 being struck down by the Courts.
Ok. I’m gonna be that guy.
This is not “Guide to global status on anti-encryption laws.”
This is “Guide to the West’s status on anti-encryption laws.”
If there were others around the world being proposed, I’m sure they’d cover it.
But since you have this view and differentiation you want to make, what does the rest of the world have that we know about that Tuta did not cover?
There are many many countries that simply follow for the most part the tech policy made by these western countries. And these smaller countries don’t have a big foothold in this space for reasons I don’t know.
Seems weird. I think they’re try to find arguments how Tuta being in Germany is an advantage rather than disadvantage.
UK & Australia in red is correct. They have laws mandating backdoors if the government requests it. Apple can no longer offer E2EE for iCloud in the UK.
But then for Switzerland and Canada they mark them as orange because there are PROPOSED laws that don’t even really mandate backdoors.
For Canada, Tuta write themselves that “While Bill C-2 does not force providers to break encryption, it leaves the option open to (future) governments to abuse this law in exactly this way. (…) The term ‘systemic vulnerability’ isn’t defined in the law. Worse, the government reserves the right to define it after the law has been passed, through future regulation. (…) Without it explicitly undermining encryption, Bill C-2 would quietly open the door for (future) governments to easily introduce secret backdoors. This could be done without requiring new legislation as long as the government asserts (based on its own undefined criteria) that these measures don’t create a “systemic vulnerability”. This is an alarming loophole that could erode the very foundation secure and confidential communication relies upon: end-to-end encryption.” In my opinion, this is a nothingburger. How can you break end-to-end encryption without creating a systemic vulnerability? You’d have to get the target person to download a manipulated client application, somehow. A future government could do lots of bad things if they want to. This is just a law proposal anyway, not a current law.
For Switzerland, Tuta write themselves that “Data must be delivered upon request in plain text, meaning providers must be able to decrypt user data on their end (except for end-to-end encrypted messages exchanged between users).” In other words: end-to-end encryption, the only relevant form of encryption for privacy, is not affected. And again, this is just a proposed law, not reality.
Same in the US, which they have marked yellow. “In the USA, end-to-end encryption can (not yet) be legally broken, however, laws like the CLOUD Act and FISA give the authorities excessive rights for data requests to American tech providers, sometimes even without a court order.” Ok so in other words, no encryption backdoors, the government can just request data that the companies already have.
Then for the EU, they cheer how the latest version of Chat Control doesn’t have the mandatory client-side scanning anymore (which would indeed have broken end-to-end encryption), but it’s still not a great law. The final version made client-scanning “voluntary”, which implicitly will encourage companies to undertake “voluntary” scanning of private messages, as it would give them legal certainty. In the context of the EU fining tech companies all the time, most companies will probably want to be on the safe side and will scan. Furthermore, a planned Commission review in 3 years could lead to mandatory scanning for some providers. National authorities may force “high-risk” services to adopt risk-mitigation tech such as client-side scanning. The only good news is that the EU Parliament still needs to approve Chat Control next year, so it could fail once more.
By the way, Tuta was in the past forced by the German government to “backdoor” email accounts (not by breaking encryption per se but by secretly copying the unencrypted emails when arriving or sending, before they get encrypted in the mailbox). How is that that not as bad as than the US government being able to tell a US company, “give me all the data you got on this guy, and don’t let him know”?
tl;dr I would classify the EU as worse than the US, Switzerland and Canada.
I wouldn’t say generally the EU is worse than the US or Asia or Switzerland and Canada, in a way it’s actually better. Maybe if we only count Japan and probably South Korea in Asia, they may be better in that regard actually than the EU but still disagree.
Here’s the thing:
What I have a problem is the fact that they’re claiming Germany is a safe haven when that’s basically has been going in the other direction.
Germany opposed chat control, then undecided, then supported then undecided then oppose and now back to supporting
Meanwhile you got countries like Netherlands, Italy, Czech Republic and one more said no/opposing even in the latest chat control proposal. And what you said with the whole German law enforcement court order to Tuta.
I would say these 4 probably especially Netherlands of the bunch is the safe haven, Not Germany.
You make it sound as if privacy tools ever existed in Japan or the Czech Republic. These countries also never appear in privacy news; they’re probably indifferent to such matters.
not even the point I was making.
I think this was Tuta’s position for a while (Europe = good, NA = bad).
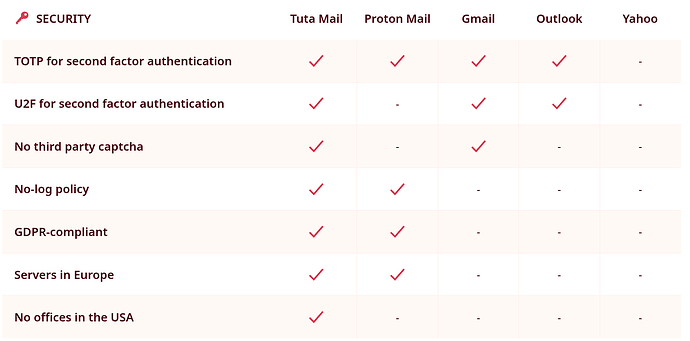
According to Tuta’s email service compassion they’re the most secure one. Partly because they have “Servers in Europe” and “No offices in the USA”.
In the article they’re not talking about Europe in general its as regime was saying, This article is basically self justifying their choice for Germany “for encrypted services” when lately for Germany its been the opposite as stated by us. Almost as if they got paid by the government for that article