I am trying to get better at threat modeling. Please share personal threat models. The strictness or intensity of your model does not matter.
Threat modelling is important because that can help you to actually manage your privacy strategies and take the correct steps to protect your privacy in you own way without going “full privacy” and blindly hardening your stuff like a prosecuted journalist, dying trying to adopt that approach, like what I did on my privacy baby steps. That’s really stressing, so this what a threat model helps you to achieve: identifying your threats so you can take the privacy measurements you actually want to implement.
These are the steps I usually personally take to TM:
- Identifying my threats.
- Reasons why I should protect myself from that threat.
- How can I protect myself?
- Categorisation and prioritisation of the threat (is this important, my life depends on protecting this?)
- And study/research the threat if applicable! To take better and informed decisions.
An example:
- Cool Spyware Inc.
- Data sovereignty loss, privacy/security loss, reduce anxiety of feeling spied on, etc…
- Avoiding their software, choosing privacy friendly alternatives, etc…
- Medium (is not a threat to my life, but I’ll get anxious if I don’t protect myself from this threat because I’ll feel that I’m being spied by this threat).
- In 2022 they handled user’s data to the government, their database has been hacked multiple times in the past, etc…
Something like that :’p I’m a visual guy, so I like to picture them as mental mindmaps.
Of course this is not a full guide on how to threat model, this is just my personal approach.
And of course, don’t get obsessed if your threat model is not perfect or you feel that’s incomplete. Over time you’ll acquire more knowledge, resources and experience and you’ll know how to threat model and how to privacy better!
If you can share what issues or concerns you’re having with threat modeling for yourself, that would be more helpful because that context and other details can explain the hindrance on your end.
An example would be SIM swap attacks. My threat model is to use my SIM number only for real time comms. This is so that I don’t tie one phone number to every service that requires a phone number. This is something to think about when handing over personal information e.g. name, phone no., e-mail, address, social media, etc.
I assume OP has already browsed these, so just to have them on hand for anyone with a similar curiosity, here’s PG’s official knowledge base articles on threat modelling and common threats (to help apply the advice).
I personally find these concrete steps from the threat modelling article helpful in getting specific:
What do I want to protect?
Who do I want to protect it from?
How likely is it that I will need to protect it?
How bad are the consequences if I fail?
How much trouble am I willing to go through to try to prevent potential consequences?
I think for example, someone not living in an oppressing regime but is concerned about the surveillance as a business model problem with google and meta would do many things to mitigate/minimize as much of the data collection as possible
for example:
- Actively check privacy settings of your phone and accounts, try disabling as much as possible to minimize it (eg. deleting advertising id and it’s one example of many)
- all together move away from google and meta and move to privacy respecting alternatives like proton, signal and mastodon
- maybe go further and debloat the phone, better yet just get a pixel and use GrapheneOS
I think it is also very important to mention the window of tolerance to associate with your move in regards to that kind of threat model:
My threat model is to not expose my data to big tech
My threat model is to limit my exposure of personal data as much as possible
Or something like those is often repeated when people try to threat model, but those aren’t threat models. They are at best vague high level goals.
A basic threat model committed in writing will look something like this:
| Threat | Mitigation(s) |
|---|---|
| Credentials compromise through database leaks | Use Passkeys (preferred) or other MFA wherever possible and use unique passwords stored in a password manager when password auth is required |
| Identity correlation between sites that should not be able to correlate my identity | Use distinct browser profiles and a VPN |
| Targeted attack by state actor using a zero day | None, risk accepted |
This is a very basic example, you can include other columns for additional relevant details if needed. The point of threat modeling is to formally list your concerns, which allows you to think about how to address each individually, and track how you plan to respond.
That’s what people mean when they say “depends on your threat model”. They are saying that your question is one for you to decide based on your privacy concerns and what you are willing to do to alleviate them.
In the above example, the “Targeted attack by state actor using a zero day” is an accepted risk, because the hypothetical person writing this threat model has decided that it isn’t worth worrying about enough to go to the lengths needed to do anything about it. Maybe they find the likelihood of it happening to them extremely low. Another person like a journalist might find it to be higher, and in their threat model it will warrant an actual mitigation like using GrapheneOS with all exploit protections enabled to harden against possible attacks.
Thank you all for the responses. I understand the point of threat modeling and the basic questions to ask. I am looking for examples so I can practically make a better model.
Here is a Purism blog article from Kyle Rankin that thoroughly defines five example threat models against various adversaries:
A threat model is meant to be made yourself for yourself for your use case and needs. Using someone else’s is not ideal nor the way to go about it. Also, there is no one right answer here so you should use what works for you and how.in
I think theyre asking for examples so that they can infer how exactly they should do it themselves, not so they can copy it. If I explain what my threat model is, how I came to it, what I do as a result of it, and so on, they can infer how they should do it themselves.
I was just about to say, agreed from here
^^, yes. I’m not looking to copy down a threat model. Think of me like an uncreative artist that is looking at someone else’s work so I can perhaps find a different, better approach to painting.
I’ll try to write one up soon. People are really misunderstanding OP, in that he wants a legit example and not an explanation.
I suspect most people don’t sit down and really draw the lines of where their threat models lie, and have it a bit hand wavy. I am also in this camp.
For cybersecurity, there are several different methodologies to choose from depending on your goal. However for privacy, I don’t believe there is a formal process, but I suspect it could easily be a subset of an existing framework or so. I’ll think about this as well when creating an example.
As a quick follow-up, I’m thinking of a modified version of DREAD, or an asset/risk based methodology like TRIKE. These are more used in cyber security, but I think a form of it could be of use here.
Honestly, the PG post on threat modelling is pretty good. With this, I’ll walk through how I think about. This is an example, and this may differ for you.
I found this works better as a “loop” then doing it all at once. This keeps the exercise simpler and can be picked up later.
- Threat: Pick one PG common threat you are concerned about
- Goal: Determine a goal you want to accomplish
- Assets: What are the assets I have related to that.
- Asset Access: How do I access those assets (and on what networks)
- (optional) Draw a general trust boundary diagram to show this
- Decide what are the risks in what I have
- Come up with an action plan with individual tasks (action items) to get to you want to be
- (optional) draw a trust boundary diagram to where I want to be
- Assign a priority to each of those action items
- Go back to step 1, going through each threat
- After all threats are done, re-evaluate
1 Pick a Threat
In this case, PG’s common threats are really great at deciding what you want to secure against.
Let’s pick a simple one: Service Providers.
2. Pick a goal
I want to ensure my digital files are stored privately and service providers can’t access them.
3. Assets
Let’s think about any asset related to the threat + goal, don’t limit yourself here!
- Google Email
- Google Drive
- Google Sheets
- Imgur for sharing photos online
- Google Photos for backing up my photos
- Now that I think about it, even my banks know where I purchase items on my credit card! But I don’t think thats related here.
- Maybe Google Translate falls into this? Not sure. Won’t worry about it for now.
4. Asset Access
Well I have a desktop computer, a cell phone, and a laptop.
For my desktop, its always on my home internet.
My cell phone uses 5G, home internet, and public networks.
My laptop uses home internet, and public networks.
5. (OPTIONAL) Trust Boundary Diagram
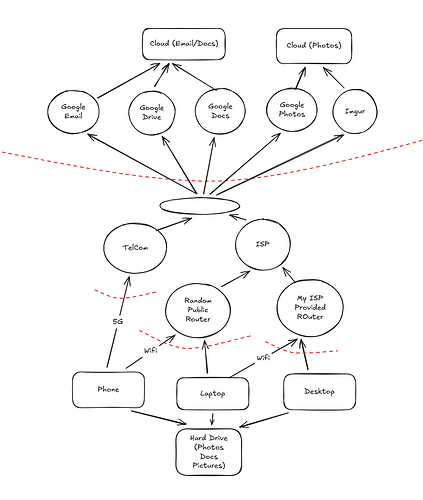
This is fun for me, but maybe not for you. For this demonstration, I believe it will help out. Here, feel free to use any basic paint program to draw this stuff. You can about how to make these diagrams as described here by OWASP. You can use any drawing application, but I really like Excalidraw for this. This is an online tool, and won’t vouch for its privacy, so I’m not putting private information in it.
On using OWASP Threat Dragon
You could try OWASP Threat Dragon for threat modeling, and it has a lot of bells and whistles. I tried, and its incredibly annoying to work with. It does seem to have a great deal of documentation in the utility available, but it seems overkill compared to a simple diagram + a document, especially since its kind of buggy.
Anyways, here is a shareable link to Excalidraw to all diagrams shown here. You can use them as you wish.
Copying some basic info from OWASP threat modeling here:
- Rectangle: Data storage. This is where data lives.
- Circle: Process, anything that handles or process that data
- Arrows: shows movement of data. You can do it two ways, but for simplicity one way works good enough for me.
- Dotted Line: trust boundary. This is where the trust level changes as information flows through the diagram.
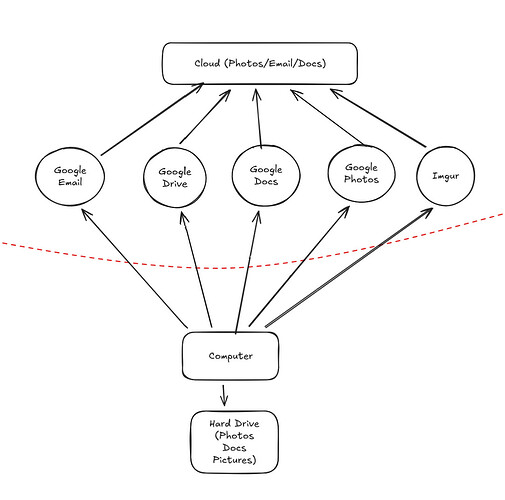
I got a little too crazy! I realize my problem has nothing to do with ISPs routers and stuff. Its mainly about me and Google. Let’s dumb this down more.
6. Risks
I’m not really worried by the router stuff right now, its over my head. I just want to make sure Google or Imgur isn’t accessing my private documents. I figured this out while I was drawing my diagram!
Here the risk is that Google is probably not encrypting my information, and they definitely analyze metadata. I think my risk here is that Google can learn more about me on things I don’t want them to. Also if they have a data breach, my information could be publicly disclosed.
7. Action Plan (mitigations and remediation).
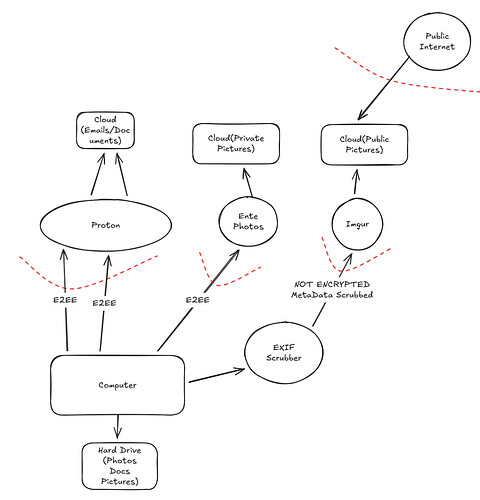
Alright, so I know if I encrypt stuff locally I could then upload that to google and be fine. But its a huge pain in the but to use PGP for emails and no one else uses it, and encrypting documents and photos locally is a huge pain and not worth it.
Well, what if I switch to Proton? They have Email, Drive, and even collaborative docs! I think this is good enough for me. I know its E2EE.
As for Photos, I know Proton does this as well, but I don’t like what they have to offer (I’m just making this up for this example). I have spare cash and I’d like to pay for Ente Photos as they have better capabilities than Proton has. I know Ente is E2EE as well. Because its encrypted locally, and Proton and Ente can’t access my data, I decide its OK to trust them as there is no disclosure of my data.
As for Imgur, I actually only ever upload random screenshots that don’t really tie back to me. I don’t really care if it isn’t encrypted, so I’ll keep using it. I’ll just make sure I scrub EXIF metadata before I upload. I know my phone has a setting to ensure it doesn’t upload this, but I usually upload stuff from my desktop. I see this EXIF Cleaner (again, an example, I’m not vouching for this one) I’ll run to be safe!
8. (optional) draw a trust boundary diagram to where I want to be
I could have drawn a trust boundary around the EXIF Scrubber, but because I analyzed the source code and I see its FOSS, I’m not bothering with that. But you could if you want.
9. Assign a priority to each of those action items
First, I definitely want to get off Google ASAP, so I’m switching my Emails to Proton right away! Then, I’ll work on importing all of my documents over to Proton Drive. After that, I’ll worry about the Ente Photos migration.
Don’t do this work yet
Track this in a document somewhere, or some todo list application.
10. Go back to step 1, going through each threat
Congrats! Take a break, as this might take some time to do and think about. Maybe you’ve got a lot of threats to cover, save your progress somewhere.
With that, now that I think about it, I saw I don’t really trust my ISP provided router, and now I’m thinking about how my online activity is generally being tracked, maybe I’ll start thinking about Mass Surveillance in my next round. I might need to use my more detailed Threat Model diagram, extend, and add some more nodes related to this.
Or maybe I’ll think about security. What if someone steals my laptop which has all of my photos on it? Could be some improvements there…
11. Evaluation
After completing this for everything, congrats! Now you’ve got a big TODO list.
Think about which of these are most important to you know. Don’t try to do this all at once. If you make your TODO list in a priority order, then you can take bite sized chunks away at the problem, and iterate on your increased privacy.
And remember, privacy is never stagnant. Even if you’ve completed your entire TODO list, occasionally revisit it and ask yourself.
I’ve been a privacy advocate for a while now and I’ve surprisingly never actually created a full-blown threat model before. I mean, I do have an implicit threat model of some sort, but I’ve never explicitly followed the steps in making one before lol
Bravo on the effort and detail. This should be a wiki!
If the team is interested, I could try to make a more formalized version on the main PG site. @ph00lt0 tagging a random team member, would a sample threat model be a useful addition to the main site?
Make a PR &/ Discussion, from there itself not just team members discussion but also community.
also you could just do @team (sorry for the twice ping ph, I thought i’d let them know another way and also alert the team)