Official reply from 1P
Hi all,
Thanks for all the questions and the thoughtful discussion. We wanted to provide a bit more context about the research and what it means for 1Password users.
A researcher identified a variation of a clickjacking attack, where a malicious website can trick someone into unknowingly triggering the autofill action in a browser extension. They reported the issue through our bug bounty program and worked with us ahead of their DEF CON presentation.
Clickjacking is not unique to the 1Password browser extension. It is a long-standing web attack technique that affects websites and browser extensions broadly. The underlying issue lies in the way browsers render webpages. After conducting a thorough review, including prototyping potential mitigations, we concluded there’s no comprehensive technical fix that browser extensions can deliver on their own.
Your information in 1Password remains encrypted and protected. Clickjacking does not expose your 1Password data or export your vault contents, and no website can directly access your information without interaction with the browser extension’s autofill element. At most, a malicious or compromised webpage could trick you into autofilling one matching item per click, not everything in your account.
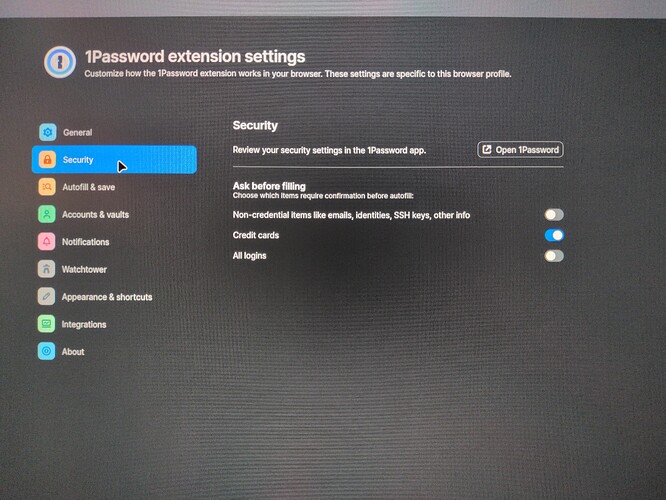
We take this and all security concerns seriously, and our approach to this particular risk is to focus on giving customers more control. 1Password already requires confirmation before autofilling payment information, and in our next release, which is already shipped and undergoing review from the browser extension stores, we’re extending that protection so users can choose to enable confirmation alerts for other types of data. This helps users stay informed when autofill is happening and in control of their data.
On the question of disabling autofill: while it might feel safer, it can actually create more risk. Without autofill, people are more likely to reuse weak passwords or copy and paste credentials into websites, where they can still be stolen if the site is malicious. Autofill also protects you against phishing sites by only working on the exact domains your credentials are saved for. In practice, for the majority of users, we believe the risk of disabling autofill is greater than the risk of clickjacking.
Passkeys are not impacted by clickjacking. Passkeys are tied to the website they’re created on and generate a one-time signature during login. That means no reusable secret is ever exposed, and even if someone tried clickjacking, there’s nothing permanent to steal.
We’re preparing a security advisory that will share more details soon.