Hey y’all ![]()
First post on Privacy Guides. And not a small one.
(If you saw my first attempt, I may have triggered the spam filter by mistake - mods, you can delete my first hidden thread)
Long story short: if you’re using a password manager with a browser extension, your data might (have) be(en) at risk.
A security vulnerability has been discovered in many popular password managers, including 1Password, Bitwarden, Dashlane, EnPass, iCloud Passwords, Keeper, LastPass, LogMeOnce, NordPass, Proton Pass and Roboform.
If you’re using Dashlane, Keeper, NordPass, Proton Pass or Roboform, make sure to be on the latest version available. They have already release updates of their apps and extensions to fix the issue.
If you’re using Bitwarden, an update (2025.8.0) is coming later this week.
If you’re using iCloud Passwords or EnPass, both have been partially fixed but are still vulnerable today. iCloud Passwords received a better fix than EnPass.
Finally, and that is the annoying news of the day: if you’re using 1Password, LastPass or LogMeOnce, you are definitely at risk. The third one simply didn’t answer the security researcher emails. And both 1Password & Last Pass have purely and simply decided to not do anything about it. More about that down below.
For now, there are three things that you can do right away to mitigate the risks:
-
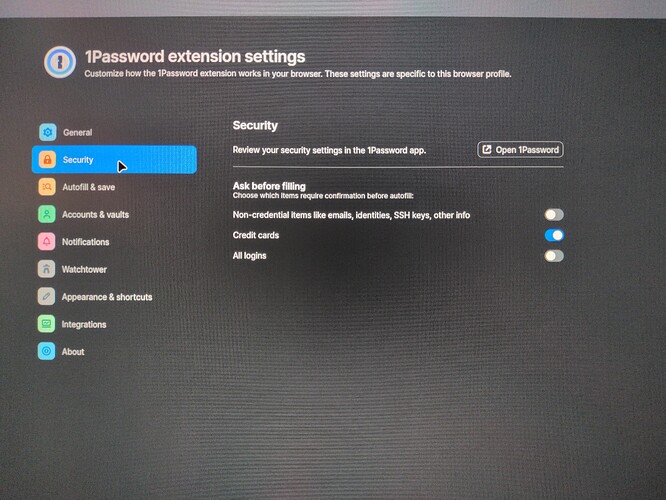
Deactivate the autofill in your extension settings
-
Make sure that the setting making sure that only an exact URL match will allow autofill credentials (Watchout tho as this won’t work for your credit cards and personal data.)
-
For Chrome and Chromium-based browsers, change your extension settings by right clicking on the extension → Manage Extension → Site Access → On click
What this will do is to make sure that your extension is only active if you click beforehand on its icon. Which leads me to the other main important point of this security vulnerability: you are at risk only when your vault is unlocked. If your vault is password/biometric locked and you end up on a compromise website, you will be safe. If your vault is unlocked, you won’t be safe.
Going back to 1Password and LastPass… What is their reason not to implement a fix for this?
For them, this is just another case of clickjacking. A form of hacking that they do consider out of their security scope. To quote from the 1Password website:
Techniques like clickjacking or deceptive overlays can be used to trick users into interacting with interface elements, including autofill prompts, in ways that may expose sensitive information.
Your information in 1Password is always encrypted and protected. Clickjacking does not expose all your 1Password data or export all your vault contents, and no website can directly access your information without interaction with the browser extension’s autofill element. At most, a malicious or compromised webpage could trick you into autofilling a single matching item following a click, not everything in your account.
For maximum safety, consider locking the 1Password browser extension when browsing unfamiliar or risky sites so autofill requires explicit intent.
The thing is that this vulnerability, relying on clickjacking (but not only), has been fixed by many other password managers like Proton, NordPass, Dashlane, etc.
This means that this specific issue is fixable. And both 1Password and LastPass have concluded that it was not critical enough to fix. I’ll let you be the judge on this, but as a long time 1Password customer, I feel betrayed and outraged by how they are dealing with this.
To quote them again, from the first article I came across spotlighting the breach discovery:
Security and usability are a balance, one that we are always making tradeoffs back and forth to find the right solution. Sometimes there is no perfect solution, only the solution that works best for the most users. As I mentioned previously, it is only with user feedback that we chose to remove the prompt for the PII items that would prevent clickjacking from occurring. A change that we’ve documented in the support article under the "Identity alerts” section.
Meaning that what works best for their users is (in an oversimplified way) to make sure that they won’t have to deal with an alert message in this case. Alas, the only kind of item that is deemed to still be “safe” in 1Password (credit cards) do involve an alert message that isn’t even correctly labeled.
To end with the conclusion quote of the researcher (and assuming it does fit your threat model):
2FA should be strictly separated from login credentials - when storing everything in one place, so the attacker could exploit vulnerable password managers and gain access to the account even with 2FA enabled.
tl;dr:
Clickjacking is not dead - browser extensions are vulnerable to clickjacking
→ iframe-based and especially to the DOM-basedMalicious script can be on any trusted website (XSS, subdomain takeover, web cache poisoning…).
XSS is not RCE, attackers can find (easily) this vulnerability.
1 click = attacker gets your credentials incl. TOTP (only for vulnerable domain)
No vulnerability is needed to leak your credit card, personal data
1 click = credit cards details or personal data (attacker’s website)
2 clicks = credit cards details + personal data (attacker’s website)
Fixed: NordPass, ProtonPass, RoboForm, Dashlane, Keeper
Still vulnerable: Bitwarden, 1Password, iCloud Passwords, Enpass, LastPass, LogMeOnceResearch on only 11 password managers
others DOM-manipulating extensions will be vulnerable (password managers, crypto wallets, notes etc. )
Finally, and assuming that it does fit your threat model:
2FA should be strictly separated from login credentials - when storing everything in one place, so the attacker could exploit vulnerable password managers and gain access to the account even with 2FA enabled.
So, yeah. Be safe out there. No system is ever 100% safe.