You forgot to post this here: @Bhaelros
For everyone else remember to always wait for all the details before speculation or straight for the throat axing a product’s reputation.
There is also this:
Discussion with 1Password
After filing the request for CVE numbers with US-CERT the Socket Security Team reached out to the impacted password manager vendors to alert them about the pending CVE assignment. At time of publication, only 1Password responded.
On a call between the 1Password and Socket Security Team, 1Password explained that the mitigations proposed by Tóth could be trivially bypassed, and that the only way to mitigate the vulnerabilities fully would be to implement a dialog popup to prompt the user before autofilling. It’s the opinion of the Socket Security Team that, if this is the case, the mitigations currently implemented by other password managers may also be bypassable.
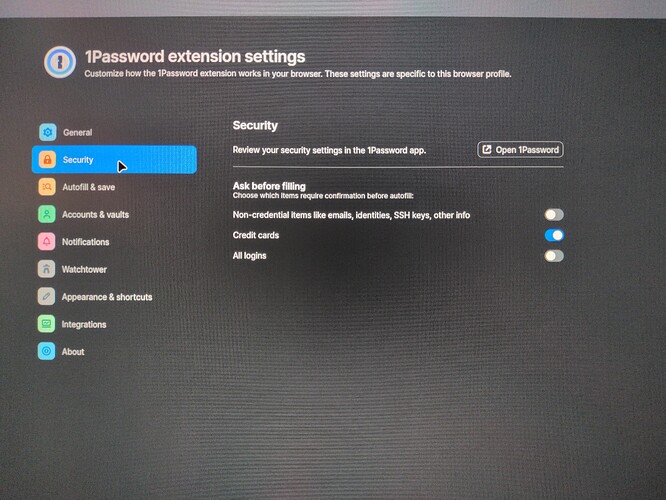
1Password stated they considered this dialogue popup solution, and implemented it for credit card fields, but opted-not to implement this for PII due to user feedback, according to the H1 triage logs with Tóth:
Security and usability are a balance, one that we are always making tradeoffs back and forth to find the right solution. Sometimes there is no perfect solution, only the solution that works best for the most users. As I mentioned previously, it is only with user feedback that we chose to remove the prompt for the PII items that would prevent clickjacking from occurring. A change that we’ve documented in the support article under the "Identity alerts” section.
As of the time of publication, 1Password has chosen not to provide an official statement to the Socket Security Research team about Tóth’s research.
While it is easy to assume vendors are simply ignoring these vulnerabilities, the reality is more complicated. Mitigating DOM-based clickjacking in a way that is both robust and frictionless for end users is a technically difficult challenge. The most straightforward solution, adding confirmation dialogs before autofilling, does introduce usability friction that some users may push back on. Password managers walk a tightrope between security and usability, and choices about which safeguards to enforce ultimately reflect product decisions about that balance. That said, the research highlights that what’s convenient for users in the short term can leave them exposed to systemic risks that attackers may exploit.
There is a fix it is in settings:
“The most straightforward solution, adding confirmation dialogs before autofilling, does introduce usability friction that some users may push back on. Password managers walk a tightrope between security and usability, and choices about which safeguards to enforce ultimately reflect product decisions about that balance. That said, the research highlights that what’s convenient for users in the short term can leave them exposed to systemic risks that attackers may exploit.”
https://socket.dev/blog/password-manager-clickjacking#:~:text=The%20most%20straightforward,attackers%20may%20exploit.
It is just not on by default.