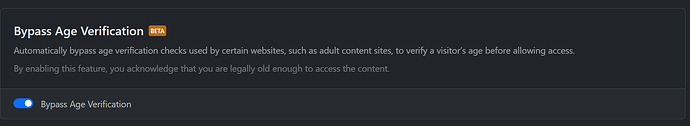
NextDNS seems to have implemented an option to bypass age verification. It can be seen in the NextDNS dashboard Settings page.
They need to fast-track this and make it stable real fast. I also wonder what kind of innovation VPN companies will take to this nonsense to help people.
Thank you for the info, I’m definitely using that.
Pretty cool.
I am wary that this feature will become the same cat and mouse game that access to streaming services features that VPNs always advertise.
How does that work?
If this AG crap comes to my country, I’ll have to sign up with NextDNS again.
Thanks so much for posting this.
I’m really hoping VPN companies themselves take action to help users bypass or get past such annoyances.
The companies who have to verify only do this because they have to proof compliance, as long as the regulator does not give a fuck they surely won’t either. The companies subject to these regulations surely do not care to actually do it as it harms their business.
Something was explained here “the service will intercept the DNS request, and route it to a proxy server located in a different country that doesn’t require ID verification.”
Or just run your own DNS server and bypass all the arbitrary restrictions imposed by ISPs and other providers. It may even be faster than your ISP’s if the latter is crowded.
Care to share a few details on this? Thanks.
The idea is to run your own recursive DNS server instead of using that of your ISP. On Linux, there are various options like Bind9 and Unbound. The exact implementation will depend on the kind of networking hardware you use. On a custom Linux router, this is trivial to implement since the hardware is under your control. If all your ISP provides is a plastic box, you will need hardware to run the DNS server, and configure the router to use that server (if that option is exposed at all). Alternatively you can configure each device on the network to use your own server manually.
The catch is that a hostile ISP might redirect DNS traffic, in which case you need to use a third party DNS like Quad9 over HTTPS or dnscrypt.
This will only work if you do the routing like nextdns does to another country.