What are these settings, exactly? I found some information from Microsoft themselves, here.
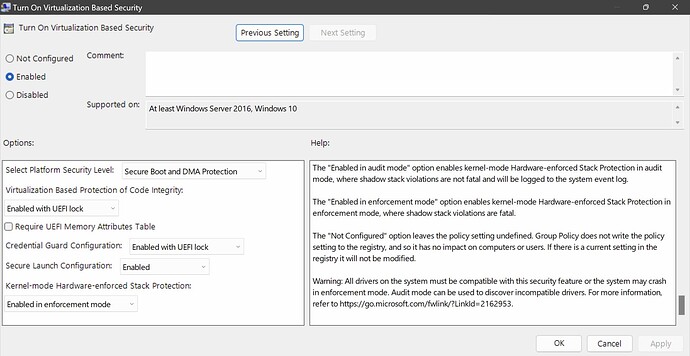
So far, I have noticed that the “Windows 11 v23H2 Security Baseline” has turned off Controlled Folder Access, placing it on Audit Mode. I manually changed this setting to Block (Click Start > type and then click Edit group policy. Click Computer Configuration > Administrative Templates > System > Device Guard > Turn On Virtualization Based Security > Secure Launch Configuration), because Microsoft says:
To fully enable controlled folder access, you must set the Group Policy option to Enabled and select Block in the options drop-down menu.
More security settings that the baseline weakened/disabled include (that I was able to identify): Apply UAC restrictions to local accounts on network logons, System Guard Secure Launch and SMM protection, Firewall & network protection notifications, Firmware protection. Furthermore, I noticed that under Windows Security > App browser & control > Exploit protection settings > Programme settings, a lot of seemingly important settings seem to be untouched.
Now, to be honest, I can’t be bothered to look through the 63 (I think) changed Local Group Policy settings, for settings that the “Windows 11 v23H2 Security Baseline” may have counter intuitively turned off. Moreover, the baseline may have not configured/missed some settings in the first place. Can anyone alert me as to settings that I should manually override/change?
In general, I noticed that some (groan) group policy security settings had defaults that were different to their recommended state (as prescribed by Microsoft), meaning they were weakening the security of my device on purpose. This begs the question, why on Earth, does this “security” baseline weaken a small number of seemingly arbitrarily chosen security settings?
Note: I noticed that Microsoft are updating their baselines, you can find updates here.
Lastly, I could not be bothered to read the “Microsoft Edge Privacy Whitepaper”, does it provide anything of importance?
Update 2: This is how I set my settings for System Guard Secure Launch and SMM protection, would you all recommend any changes?