Hey, I wanted to know your thoughts on iCloud Private Relay, does it actually works and secure or we should have to use VPN to masks your IP address and browsing activity.
It’s only best if you use Safari and it doesn’t cover any of your system apps.
Depending on what you’re looking for with a service like private relay, it’s still best to go with a dedicated paid VPN service like IVPN or Mullvad.
If masking and obfuscation is what you need, then you definitely need a proper VPN.
It’s great for Safari and mail, doesn’t cover all traffic on the system though. It’s a bit more than a regular VPN though, it uses two hops by two separate parties: Apple and a rotating set of third party providers, so neither Apple nor the third party know both your real IP address and where your traffic is going. It also uses blind signatures to authenticate so they can’t correlate your Apple account with your traffic. It’s a really great system I’d say the only issue with it is that it only covers Safari and mail basically.
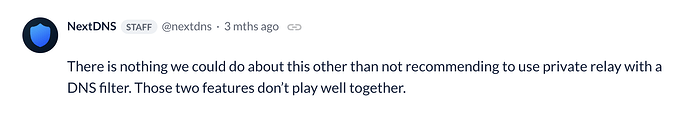
Using NextDNS myself, they don’t advise using Privacy Relay if NextDNS (or any custom DNS) is setup.
Even tho it does provide a nice (free of charge) security layer, Privacy Relay can and will also leak your DNS. It only works in Safari and Mail, but since most of iOS users are relying on Safari on a daily basis, it may causes some random problems or purely and simply leak your DNS (and so leak some of your private data).
If you’re not using anything else, it’s better than nothing. It’s a thin security layer, which can’t hurt the common person. If you do use custom DNS or a proper VPN tho, deactivating it is very much advised. Either way, Private Relay is not a VPN in itself. If you want to protect your privacy, a VPN like Mullvad or Proton is the way to go (the latter is getting better and better btw).
In any case, never forget that all of these aren’t providing a system wide protection. The way iOS has been developed allows some of the Apple services to purely and simply call home. And so, ignore your VPN.
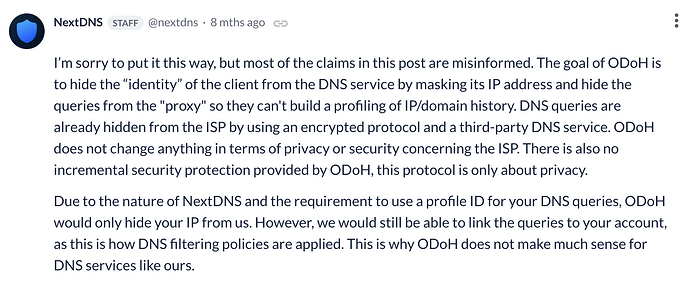
I was under the impression it uses ODoH systemwide unless you override it, is that not the case?
Even if it is the case (which I do believe, yes), using a different DNS provider than your VPN’s default is a potential web fingerprinting factor, and ODoH wouldn’t change that.
You can do the test by yourself, but many NextDNS users (me included, also with Quad9) noticed that there was almost systematically a DNS leak happening with iCloud Relay turned on. There are many comments on the NextDNS Reddit in that regard. Oddly enough, it doesn’t happen on macOS. Only on iOS.
There’s also a bug that the dev behind NextDNS tried to “fix” (meaning begging) Apple to fix.
And when it comes to ODoH, NextDNS didn’t and won’t implement it. As jonah stated while I was writing this message, ODoH wouldn’t do much anyway.
As far as I know, the guys behind NextDNS really got in touch with Apple to improve things.
Alas, there’s much more they can do besides waiting for Apple to update their priority list…
Yeah because NextDNS built their service around user accounts ODoH wouldn’t do anything, which is why I’m not a fan of NextDNS personally. No other DNS service requires an account that I’m aware of, like they said it makes it very easy for them to correlate your DNS requests with you. The new network filtering stuff in iOS 26 will make DNS filtering obsolete anyway on iOS so I’d say once that’s out you’re probably better off just using Private Relay’s DNS. It’s a shame about that bug and the leaks, really shouldn’t happen and I hope they fix that.
I remember reading somewhere (maybe here) that these new network filtering features would only be available for managed (MDM) devices. Was I misinformed?
Nope just a regular API that app devs can use:
I view it as suspicious. Anything Apple or Big Tech in general tends to be closed source, and as such, it is impossible to verify any claims made about security and privacy. For all that matters, Apple can just log all your DNS queries and sell them to data brokers. I run my own recursive DNS server instead. Another option would be to use DNS over TLS to a DNS provider that you can reasonably trust like Quad9. I don’t see why you would need anything else.
Well, one can reverse engineer it: TrustMeRelay? Investigating Apple’s iCloud Private Relay - YouTube
Besides some hard to mitigate issues like the config distributor still being Apple, it’s designed pretty solid.
it works properly on Safari, does it able to hide IP?
okay, so we can access region restricted content with this?
Hiding your IP from whom? The website or your ISP or someone else?
both
Using a proper VPN is best in that case. It’s just a full fledged solution and a better option if you ask me.
That’s not really the goal of iCloud private relay. You don’t have the option to choose a wide range of locations. You can either choose a server in your area, or a server that’s in the same country and timezone.
thank you ![]()
alright, I understood, thank you ![]()