Hi all, I wanted to thank everyone who participated in this thread — and I’d like to clarify my position, especially regarding the mention of TEMPEST attacks and side-channel threats.
I’m not trying to suggest these attacks are common or that they’re actively targeting most users. What I am doing is:
-
Operating from a high-threat, high-integrity model where air gaps are essential.
-
Trying to eliminate covert vectors that rely on firmware, side-channels, or invisible interference.
-
Acknowledging that modern side-channel research has evolved, and I want to design defensively.
Here are some specific clarifications, with citations and brief takeaways:
TEMPEST ≠ Fiction
The idea of electromagnetic side-channel attacks (“TEMPEST”) is very real — though mostly applicable to specialized threats.
“TEMPEST is a codename referring to investigations and studies of compromising emissions.”
— Wikipedia: TEMPEST
Historically, this meant Van Eck phreaking of CRTs. But today, researchers have shown more subtle and powerful methods using modern tech.
This 2021 peer-reviewed paper showed that electromagnetic emissions from mobile phone screens can be intercepted — even without line-of-sight — and used to reconstruct the display contents:
“Screen Gleaning: A Screen Reading TEMPEST Attack on Mobile Devices Exploiting an Electromagnetic Side Channel”
– arXiv 2011.09877, NDSS 2022 Paper
Key findings:
-
Passive EM leakage from the display driver can be captured with an antenna and SDR.
-
Machine learning models reconstruct gray-scale images of what’s shown on screen.
-
Leakage is observable even with no physical access.
So yes, it exists. And no, it’s not widespread — but it is technically feasible under the right (wrong?) conditions.
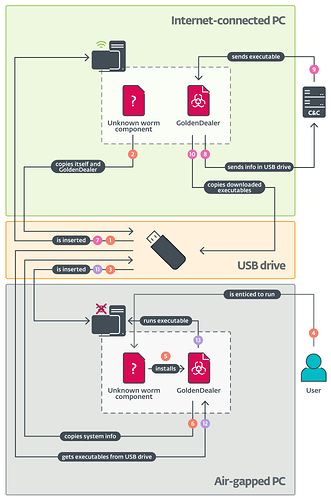
For those concerned about air-gapped systems (like me), here are things worth considering which some of you already suggested, thank you for that confirmation 
• Firmware infected USB Drives:
Use optical data diodes or burnable optical media (CD-R/DVD-R).
• Side-channel / EM leakage:
Place sensitive systems inside a shielded (Faraday) enclosure, or use passive analog output (e.g., e-ink displays with no backlight).
— the e-ink display is definitely one that I consider to implement. Especially since they matured a lot last year both in size and functionality.
• Powerline interference / EMI:
Use isolated battery banks, avoid shared grid connection during sensitive operations.
• DNS spoofing or MITM in compromised system:
Use air-gapped mirror of DNS root zone, or hardcoded .onion or IP map. Validate all packages cryptographically.
ATM my mind is foggy, but I’m trying.
Due to ongoing DNS spoofing (cross device, cross borders, different systems that never co-existed in the same environment), I don’t trust my searches to return real results anymore. I’m offloading this effort to a known air-gapped system I’m rebuilding from scratch — bit by bit — but it takes time and care. That’s why I came here: to leverage the collective insight of this community.
Thanks for understanding.
I’ll post more detailed notes on secure file transport, but in short:
USB ≠ safe anymore. I’m exploring CD/DVD, RS-232, optical transfer, and more radical “clean-room” approaches. I’ll post findings once I can validate them from an uncompromised setup.
If anyone else has experience defending against low-level firmware, EM leaks, or optical-exfil risk, I’d love to hear more!
Edit: The end goal is moving away from Linux and switch to a BSD system for obvious reasons. The current state of Linux is unsustainable, but it requires from my perspective a whole lot of effort to master it, all while dealing with information that I can’t trust as genuine, due to the DNS spoofing on ISP level, faked and manipulated Cert Stores on any device that I touch and the very limited information that I “may/can” access is often well over a decade old if not 2 decades.
![]()