If you are located in a civilized, human rights respecting country in the western hemisphere, you should probably not be using a VPN[1].
[1] except on public WiFi and untrusted networks, which you should avoid using.
While I have found that the recommended VPN providers {Mullvad, Proton, IVPN} likely stick to their promise of not storing logs, they are flawed.
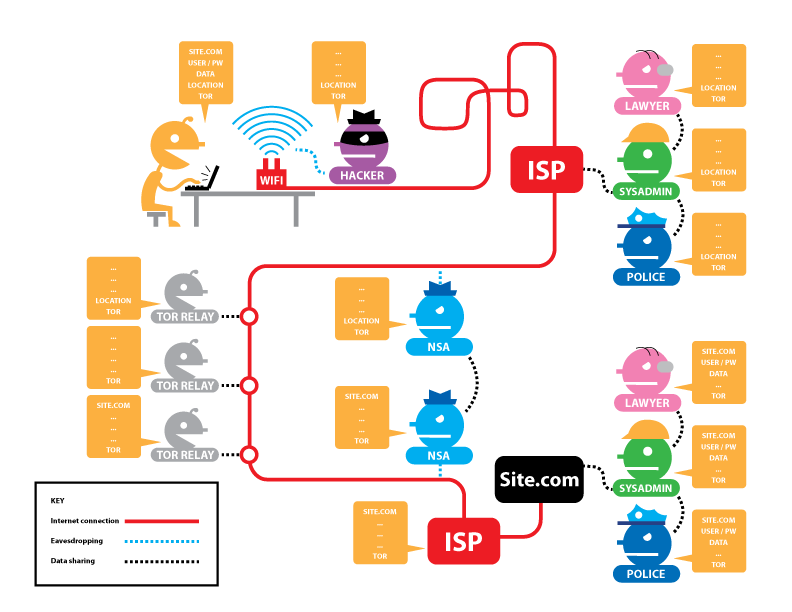
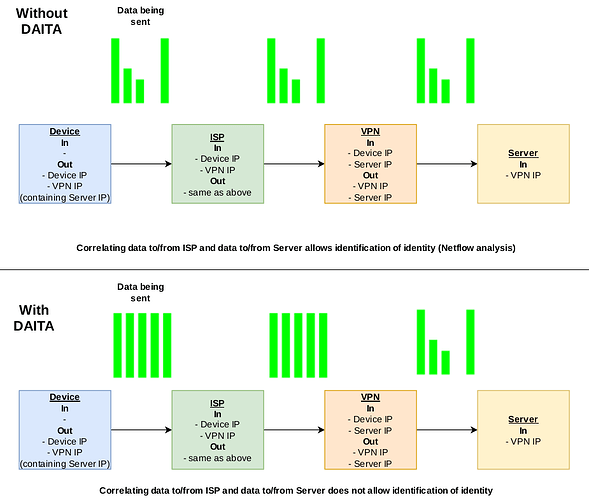
Every single VPN company on the planet depends on upstream networks out of their control. Proton operates a small network for their Switzerland servers, but there mere fact of connecting to them may still expose you[2]. I have reached out to several of their common upstream networks {M247 Europe SARL, Datacamp Limited, 31173 Services AB} with a simple question: do you collect NetFlow data? For how long is it retained? Do you share it with third parties (especially government agencies)?
The answers I have received have personally upset me: not a single provider responded saying they do not collect NetFlow data. One of the providers indicated NetFlow data is stored as long as 90 days. Only one of them was willing to answer whether NetFlow data is being shared with third parties, which they supposedly do not.
[2] Switzerland enacted a law requiring network operators with connections to other countries to mirror all traffic to the government. If you connect to a Switzerland based VPN server from outside Switzerland, you are making yourself blatantly visible to them.
To sum this up, 90% of all VPN servers have upstream networks collecting NetFlow data, sufficient to identify and match users to their traffic. In many cases, the (legal and especially technical) obstacles for monitoring individuals are significantly lower when using a VPN.
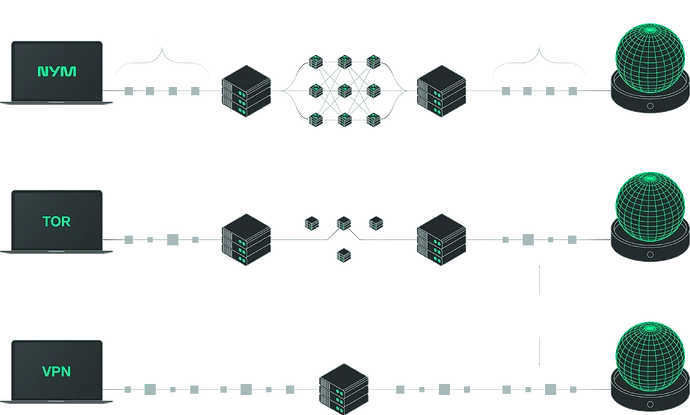
In light of this, if you need to remain anonymous, use a multi hop setup through jurisdictions that do not aggregate their NetFlow data. For example, routing traffic through a middle node in Russia or China can break the trail.
The battle for anonymity has long been lost and I am tremendously concerned about the implications this will have on the future of democracy.