Virtual cards depends on your bank, right? I don’t know how someone can get totally non-trackable virtual credit card.
mm yes but there’s privacy.com, revolut, wise that provide virtual cards, and in my experience using them I never had to provide a real billing address or name to any company, that’s just my experience.
Of course the other side is valid, damn KYC.
Privacy.com operates in USA only I think.
Revolut has all the information about me (EU), same with Wise. I gave them my passport and ID card copies, and did a facial verification. Considering they are operating as a bank I don’t think they will protect me in case of some legal entity wants my real identity ![]()
Edit. If Proton could have provided Gift Cards via Amazon, like Mullvad does, that would solve a lot of issues but they are not doing that. I don’t want to send hundreds of Euros by post, considering how easy they are getting lost, and paying with BTC is not anonym, and have higher costs.
And then we wonder why some accuse privacy (especially or rather exclusively VPN) companies as selling snake oil. PG (both the community and the website) is right to call it out should stay away from those.
This topic is on a privacy-focused VPN app, not an rich person’s aerodynamic race fantasy death shell.
Edit
If I had a dime for the number of times I get sent this screenshot because my app is “leaking DNS” …
![]()
You would have 2 dimes which is not alot but strange it happens?
It isn’t strange. Mullvad isn’t immune from misleading marketing and alarmist claims. Recently, Graphene also called them out for their “VPN leak” claim not that long ago.
Better 2 dimes than £5 earned by spreading FUD.
I was trying to make a reference but thanks for your input!
One reason the Proton products exist is to make privacy and security somewhat automatic so that ordinary people can use them.
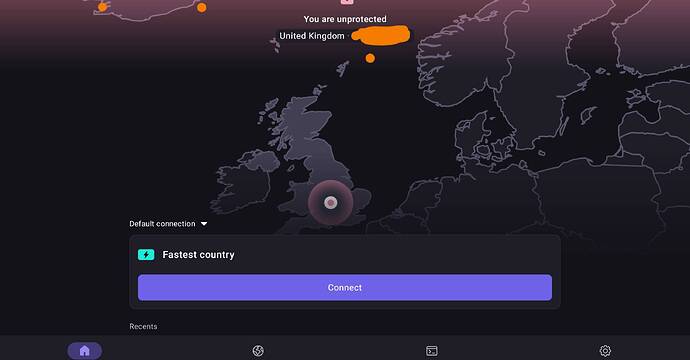
In technical contexts words like “connected” can be vague and confusing to people who don’t understand the technology.
A word like “protected” may be slightly alarmist, but if you go on the assumption that people with the app already want to “protect” their connection against some type of risk, then “Protected/Unprotected” is more clear than “Connected/Unconnected”.
For example, a non-technical person may hear “unconnected” and not know whether it means their phone has no bars of service, or the app can’t reach Proton’s server. Whereas unprotected makes it clear the VPN function is off.
On iOS these settings are under the “usage statistics” menu, although it uses the “unprotected” verbiage on the home screen.
I do not take issue with the use of “unprotected” instead of “disconnected,” I don’t think it crosses a line (for the reason @benm just stated above actually). However, I agree that it is important for settings to be clearly labeled.
I can’t reproduce on my end…
I do see that the version number on your Proton Mail app is 5.10.32.0. As far as I know, the latest stable version on the GitHub repository is 4.9.0. Are you using the Google Play beta release of the app?
Can other community members reproduce the behavior in the OP with a stable release downloaded from GitHub?
Edit: Somehow glossed over that this is not for Mail but for VPN. Embarrassing mistake by me. Sorry for all involved ![]()
I have not personally confirmed this behavior on my own phone yet, but this version is the current stable/non-beta release on Google Play.
Edit: Also note this is VPN not Mail
The behaviour refers to the ProtonVPN app, not ProtonMail
5.8.24.2 and I can replicate…
Nate Graham from KDE world spoke about how he thinks they rolled out telemetry poorly so they got the worst of both worlds by making it opt-in and with the default setting to share nothing. It’s one of those things that sounds good on paper but it makes development that much more difficult, since most people will not explicitly opt-in, but it makes a real difference in their ability to triage bugs, find crashes, or justify adding or removing development resources.
In my opinion, telemetry is a threat model question and if your threat model doesn’t need to remove telemetry, you should leave it on and help the developers make the software you use better.
Back in the day where spyware was rampant and we regularly ran spyware scan tools, we built habits around maximum opposition to telemetry, which makes sense, but zero telemetry at all can make it difficult for developers to actually make improvements.
Ehh, it’s anonymous telemetry, you can also check what’s being sent yourself. I don’t see how it’s an issue for any threat model.
But yes, I agree that opt-in telemetry is pretty much useless because almost no one will ever opt in because the privacy community is still full of alarmists screaming that all telemetry is bad and should be disabled.
As others have mentioned, I think this is really semantics issue than anything else. And therefore highly debatable.
I don’t believe Proton is trying to mislead anyone here.
The thing is, even after turning off the telemetry under the so-called “Help us fight censorship” menu, the app still tracks you.
Really? “Anonymous” data can be “de-anonymized” easily.
That is like saying “Developing free and open source software is pretty much useless because no one will ever donate. Better to make a proprietary app with a ton of pop-up ads in it”.