Session is no longer just a Signal fork, and recently announced that they are bringing back PFS, while adding Post Quantum as well.
I would not use a messaging service. I would probably send them a pastebin equivalent link that destroys after one use.
I am not sure why messaging apps are in consideration here, are you unaware of other tools that can be used for ephemeral sharing? To someone with hammer, every problem is a nail, but the fact that hammer is the right tool for the task is not certain.
I’m only bringing this up since no one mentioned it: Onionshare has a chat functionality where you can communicate over Tor. This may not be easy to use and set up but is certainly an option that is a solution to your ask.
You can use a FE with no tracking/account here
Correct, that’s why I recommend using it exclusively with Tor. I’m not sure what device your using so the exact steps you’d take are different. But assuming anonymity is key, I’d bet Tails would be a good option. If you needed it on a mobile device then using a dedicated GrapheneOS profile with Orbot set to always on before installing SimpleX Chat might be the way to go.
In your OP you mentioned not using a VPN so I’m not sure if you’d extend that to Tor. I can’t imagine a scenario where you would want to prohibit yourself from using Tor independently from a messenger but if you have a legitimate reason for avoiding it, then I suppose it’d be between Cwtch and Session.
Cwtch uses the tried and true Tor network and I believe it is metadata resistant, but it isn’t completely cross-platform and it hasn’t been audited yet. Session lacks PFS and uses its own Lokinet which may not be as anonymous, but Session is cross-platform and was audited. Again, I think Tor + SimpleX Chat is definitely the way to go, these are just some alternatives if that wasn’t possible for some reason.
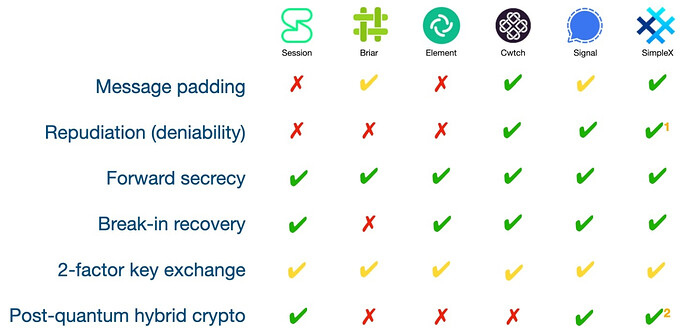
One of the main benefits is its lack of identifiers. There might be more to it than that covered in their whitepaper. They also made a comparison chart of E2EE which I believe is still accurate for Session vs SimpleX Chat at this time.
Attacker with access to hosting providers and ISPs implies malware.
Targeted attack would not target the server but the endpoint. Snowden has said the NSA routinely targets endpoints to exfiltrate keys and messages. So let’s scroll through the tiers if you will, so you get the idea of attacker capability vs defense at each level.
A) Completely unencrypted messengers like MSN Messenger, Palringo → You eavesdrop the traffic from backbone (NSA UPSTREAM program etc.)
B) TLS encrypted messengers like XMPP, Telegram → You subpoena or hack the server to read logs
C) End-to-end encrypted messengers like Signal → You hack the endpoint and read messages from device. You might perform invisible MITM with exfiltrated identity keys.
D) Torified, end-to-end encrypted messengers like SimpleX over Tor → You discover the endpoint with traffic correlation attack and confirm it with confirmation attack: basically cut power to suspected house and see the person disappear from group conversation you’re monitoring as member. Then you hack the endpoint and exfiltrate keys and plaintexts.
E) Torified p2p messengers like Cwtch → Without public groups you first somehow befriend the target or add them as contact, and while communicating with target, perform end-to-end correlation attacks using known plaintext sizes over time, and then do traffic confirmation attack if needed. Once you obtain their IP address, you remotely exploit the endpoint to exfiltrate keys and plaintexts.
F) TFC Qubes configuration → Like SimpleX/Cwtch you establish endpoint IP and remotely hack the device. You then have advanced targeted malware that either breaks out of Xen VM isolation to pwn dom0, or you insert malware that runs on Destination VM, to establish return channel via Qubes’ RPC queue status value, to exfiltrate keys from RAM of destination VM running TFC’s Receiver program.
G) Torified messenger using smart cards or other reduced TCB / HSM for encryption (E.g. PGP with Yubikeys) → Like SimpleX/Cwtch you establish endpoint IP and remotely hack the device. Keys probably stay safe in the secure cryptoprocessor of the smartcard, but you instead lift logs and/or eavesdrop on the plaintext input/output, basically with screen logger that sees the conversation. The smart card does absolutely nothing wrt plaintext IO.
H) Torified airgapped PGP → Like SimpleX/Cwtch you establish endpoint IP and remotely hack the device, you cross the airgap by hiding extremely advanced malware to USB headers that pwns the low level OS stack and that exfiltrates keys from the airgapped system. Even if you chain this with Yubikey, the malware can still sneak plaintexts from the airgapped device when you move an outgoing ciphertext to networked computer for sending.
I) TFC (split TCB over hardware data diodes) → Like SimpleX/Cwtch you establish endpoint IP. The data diode prevents key exfiltration by preventing insertion of malware to Source computer, and it prevents malware on Destination computer from exfiltrating keys. But you still have options.
-
You exploit the Destination computer and use some unaddressed covert channel (options listed here) to exfiltrate keys,
-
You park a van with strong antennas and eavesdrop on the keyboard and display cables of the target computer. ( Van Eck phreaking - Wikipedia , https://en.wikipedia.org/wiki/Tempest\_(codename) ), or
-
You interdict electronics shipping or break into their home and install bugs to the computer (see NSA implants for retroreflectors in USB and display cables: RAGEMASTER, LOUDAUTO, and CONGAFLOCK under ANT catalog - Wikipedia ) or you install hidden cameras/mics to the space
Here’s the thing. There are technical ways to protect you from more or less all types of mass surveillance. TLS defeats backbone collection, E2EE defeats server-side eavesdropping. TFC defeats attempts to automate endpoint exploitation (think one chain of zero days against all Windows11s, or Ubuntus, defeats a great deal of endpoints until patch is deployed).
But as you saw above, no messenger is 100% secure against targeted attacks by the most sophisticated adversaries out there. Even TFC was written (full disclosure: by me) to deal with mass surveillance and remote attacks. Not close access operations. You can add wild stuff to make yourself a harder target, from monitoring your home with cameras, to blankets, to EMF shielded cases (TEMPEST validation is left as an exercise to the reader), and to connecting from random Wi-Fi access points with long range parabolic antennas ( Wardriving - Wikipedia ), but unless you’re Edward Snowden on the run, I’m unsure if that’s worth your time. Sometimes the best strategy is to just Signal someone to meet somewhere, and when F2F, communicate by writing the private details on paper instead of saying it out loud (See the ending of Citizenfour documentary).
But, the thing is, the novelty of this spycraft stuff wears out. Fast. For anyone. For everyone. It’s a short-term mitigation aid, not a long term strategy. It’s that which you and your buddies can’t sustain forever, that sets the cap for your overall communication security. If you’re a dissident in an authoritarian country and your life depends on it, sure, dial this stuff to eleven. But if not, don’t expect your buddies to exchange one time pads via dead drops weekly. (:
I added SimpleX to the table with the appropriate context.
For the most parts SimpleX is a fantastic decentralized messenger with very strong privacy protection. You can see some comparisons, for example:
Yeah the table is anything but up-to-date.
If SimpleX can enjoy green tick mark for repudiation and PQ-security, so can Session for forward secrecy that is being implemented. I get that it’s an older comparison but again my point is it’s no longer valid. (Also, IMO one shouldn’t advertise planned features as features until it does that for all users by default.)
Saying Signal doesn’t offer deniability is really weird. It has had MACs instead of digital signatures since forever. Signal builds over OTR protocol from 2004 that had deniability as one of the the main selling points.
Cwtch has deniability too Cwtch Technical Basics | Cwtch :
This exchange (documented in further detail in authentication protocol) is offline deniable i.e. it is possible for any party to forge transcripts of this protocol exchange after the fact, and as such - after the fact - it is impossible to definitely prove that the exchange happened at all.
Signal not having break-in recovery, i.e. future recovery is laughable. That’s the first bullet point when listing properties of Diffie-Hellman ratchets. This also applies to Element and Session that use double-ratchet like Signal. Nowadays, even Signal’s post-quantum protocol has sparse ratchet.
Calling public key fingerprint verification “2-factor key exchange“ is nothing short of weird and uninformed. Briar has it equally strong as SimpleX does, you scan the QR-code that authenticates the onion service address.
And SimpleX is as weak. It also allows sharing the contact link over channels where the user doesn’t have strong authenticity check. Privacy & security admits this:
While SimpleX Chat always establishes connection via link passed via an independent channel, so it is already more protected than other apps, there are scenarios when the invitation links can be substituted in transit (MITM attack). To protect against such attacks, you should verify the security code with your contacts:
So SimpleX can be also used without requiring strong authentication so they deserve yellow mark. Session ID is also similar identifier and that can be replaced by MITM too, as is cwtch ID, so ALL messengers here should have yellow check mark. Or green. The only way to prevent this is to require QR-code scanning and prevent screenshots. Which kills uptake. I think more important aspect here is fingerprint nagger that keeps you informed about whether you need to get it done. Back in TextSecure days Signal had visible status in the top bar similar to OTR for Pidgin. I’m unsure if it was a wise decision to hide it.
Finally, post-quantum crypto, Signal has it. Session has it planned now.
This is probably most of it. Anyway, here’s an updated table
I greatly appreciate all the responses. I mostly consider usage on GrapheneOS, for context.
In my opinion, Tor is extremely buggy on Graphene (might just be Orbot), hence I think using a VPN would indeed be the better choice here
I still have a few questions
- Why (in most of everyone’s replies) SimpleX over Session?
- How significant is, in terms of anonymity, Signal’s servers being central in the USA on AWS?
- Why do you guys think Signal >> Government Communication has been silent for a while? (not implying anything by the way, just curious)
Now, to respond to the most people I can:
@anon69871701 and others suggesting sending pastebin links or paper mail - my original post concerns messaging apps, the scenario given is just an example but I aim to filter out for the best messaging app
@maqp Thank you for the extremely in-depth analysis of each possible scenario, but the question remains - which of the messengers do you recommend? Obviously many things can happen with such adversaries but I still need at least the best case solution
From the current replies, I got the idea that Signal (via the molly client) is the best option?
SimpleX over Session iff you use it over Tor. Tor’s anonymity network is much bigger making end-to-end correlation etc much more difficult.
Signal has plenty of court subpoenas listed at the link you shared to show it does not collect your comms metadata, so not too bad. If some nation state hacks Signal’s servers, they can eavesdrop on the metadata. Thus, Signal isn’t for anonymous communication. Look into Tor Onion Service based messengers for that.
Because feds know they don’t get anything from there. It’s highly unlikely nation state hackers share that information with feds to prosecute criminals. Capability like this would very likely be SCI. But it’s dangerous to speculate. Again, if you need technical guarantees for anonymity/metadata, use something else than Signal.
E2EE for daily use: Signal. Just check the safety numbers.
E2EE + metadata: If you need to hide who you talk to, Cwtch. Also, Quiet might also be pretty good especially for group chats as it seems to have focus to act as slack replacement.
If you absolutely need offline messaging and everyone around you is a hardcore cypherpunk who knows how to install Tor, configure proxy settings, and verify those settings work, you can get away with SimpleX using self-hosted onion server. That way you avoid the main issue of being able to accidentally deanonymize yourself when connecting to peers via the closed server.
E2EE + metadata + endpoint security: TFC for those who know they’re dealing with state sponsored hackers. It’s not pretty, it’s not fun to use. But it’s the only thing that does a damn thing about endpoint security with more than trying to write secure code.
Those are IMO the best options in the larger, architectural categories.
And if I use VPN instead of Tor?
Probably works if your adversary is the messaging app service provider or tiny government that plays by the book. Not a good idea if it’s an authoritarian government that could hack the VPN service provider, subpoena VPN company’s logs, if the VPN is a honeypot or something that sells you out to avoid prison. VPN is just another ISP, that instead of your router IP and household browsing habits at IP/DNS level, knows your browsing habits on per-device level. They might have solid mission for privacy out of principle (e.g. Mullvad looks decent), but they will never, ever, ever go to prison for you. Not advocating crimes here but hiding Jews in your attic was illegal once, now/soon it’s hiding latinos from ICE.
It is possible it is referring to the groups? ref: Signal Groups V2 is a privacy downgrade
The differences between Groups V1 and Groups V2 seem to be:
- Consistency issues: Problem in V1. Solved in V2, which allows Signal to greatly improve the UX and feature set of groups chats.
- Group participants (by IP address): Probabilistically discoverable in V1 with timing analysis. Known by the service in V2.
- Group administrators (by IP address): Secret in V1. Known by the service in V2.
- Group participation deniability: Deniable in V1. Non-deniable in V2 – the service has mathematical proof that someone with your IP address is a member of the group.
If I remember correctly, Threema is maybe the only messenger that has fingerprint verification warnings baked into the contacts list UI in-app. I could see this being something Molly (a hardened Signal client) might be interested in.
So you are saying SimpleX over Signal, why exactly?
Group membership deniability is not the same as message authorship deniability (done with MACs), which is what deniability usually refers to.
Yeah those three dots on contact list and below contact’s name in chats probably refer to authentication level. I wonder if the program name refers to three message authentication levels.
(TFC also has it visible but only on contact listing)
If you can, you should definitely propose that to them. At least as an option to make it visible.
Because Signal is content-private by design, and metadata-private by policy. Signal requires the user jumps through much more hoops to use anonymously like obtaining a burner device, and a non-KYC prepaid SIM, and it’s not catering to users using Tor by bumping them to onion service based server if Tor is being used. SimpleX can be used anonymously at least on desktop, if you install and launch Tor, and configure SimpleX to use Tor before even registering your user. That’s more private than Signal.
(This may sound controversial given my critique towards SimpleX. But. My issue with SimpleX is not what it can do when configured properly. It’s what they don’t do by default. They claim to be more private than Cwtch that by default not only uses Tor for everything, it doesn’t even have (de)centralized server but is p2p.)
This is the official word:
Threema started life as an abbreviation: “EEEMA,” for “End-to-End Encrypted Messaging Application.” The three “E”s were a bit unwieldy, so it became “Threema.”
It is enjoyably simple, even though your suspicion would have been more interesting.
Do not do this. It is highly unlikly you will be able to send that letter without sending your dna along with it.
Can someone, preferably @anon63378639, explain why Conversations is never recommended in any of these threads for Android to Android chat despite being the recommendation here: Messengers - DivestOS Mobile
If the threat model isn’t high, how would Conversations rate against Signal or SimpleX? I find Signal chews my battery on GrapheneOS.
Is it purely because it’s only on Android that it isn’t recommended?